Wij richten ons op identiteiten– en toegangsbeheer
De basis voor cloud-security, access en compliancy.
Een aantal van onze cliënten

Bedrijfsprocessen die tot in de puntjes door ons ontzorgd worden
Provisioning
Geautomatiseerd rechten verstrekken op basis van functie, rollen of zelfs kenmerken.
Security
Altijd auditeerbare en actuele basis-gegevens voor uw security infrastructuur.
Access
Toegang tot bedrijfsmiddelen op de juiste momenten, door de juiste mensen. Toegang die ook met self-service mogelijk is
Cloud
On-premises, hybride of volledig in de cloud. Afhankelijk van de eisen en wensen van de organisatie
Volledige controle
over uw ICT
infrastructuur
Trusted-ID heeft een standaard framework voor Identity and Access Management, waarbij de belangrijkste systemen zoals HRM en het AD aan IDM gekoppeld worden. Via entitlement management kunnen we uw autorisatie management voor eens en voor altijd goed inrichten.

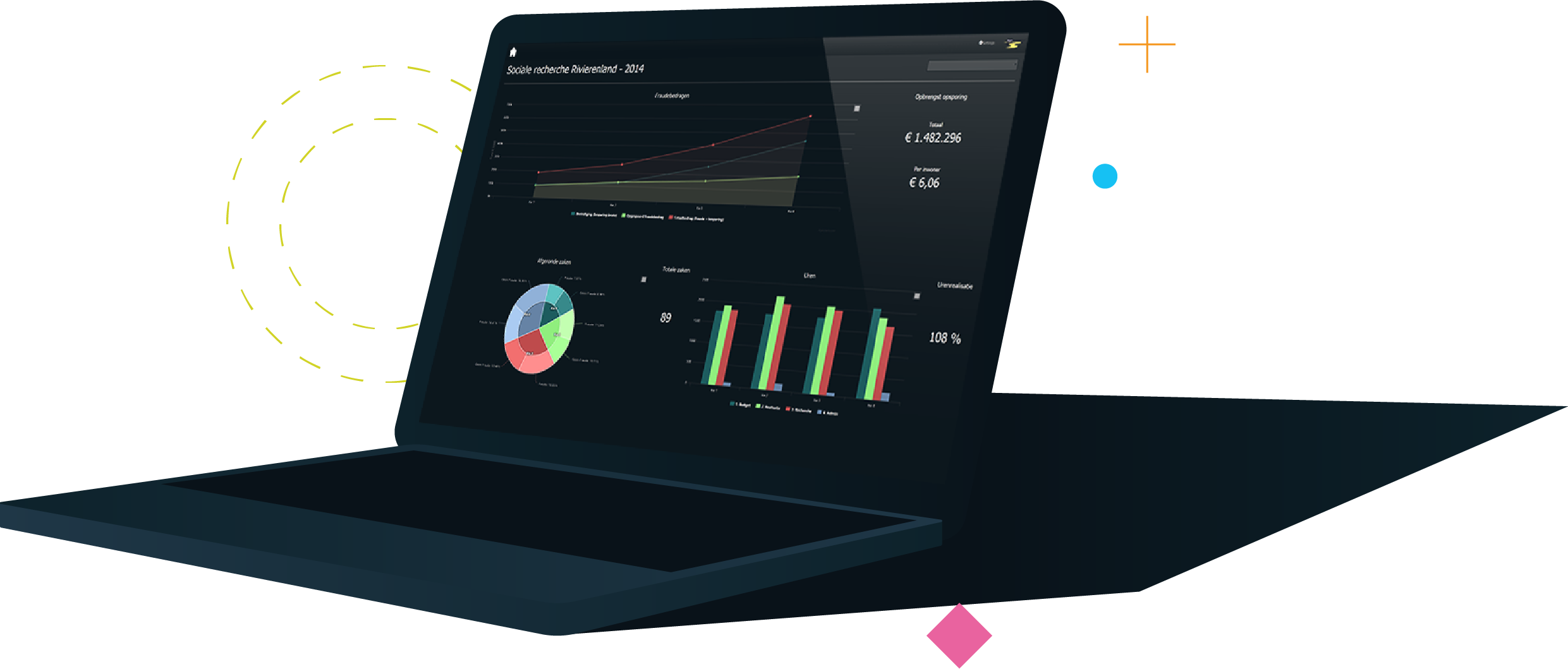
Wat gaan we
voor u doen!
Trusted-ID is een end-to-end leverancier van IAM. Wij leveren alles wat nodig is om uw IAM infrastructuur te realiseren en actueel te houden.
Onze diensten

Benieuwd wat wij voor u kunnen betekenen?
ma t/m vrij 09:00 – 17:00
Neem contact op via





